~~Update; 16 Jun 15: Switched back to v2.3.0 as I'm suspecting there are better html resource allocated to the GUI front end. I am now not getting as many reboots.
~~Update; 31 May 15: Was having issue with the MK5 locking up, PineAP shutting off, and ICS with Mac inconsistent on its own on firmware 2.3 and ended up switching to 2.2. Still getting the lockups, PineAP shutdowns and ICS inconsistencies so moved to 2.1.1. I also switched to Kali linux as my system linked to the MK5 instead of my Mac. So far I've been having better results. I starting to suspect its my Mac.
~~Also read here (
https://forums.hak5.org/index.php?/topic/35117-release-23x-codename-logasaurus/) that v2.3.0 firmware "Finally an improved wireless tethering system has been implemented,
allowing one to share an Internet connection from a client device - such
as a laptop or rooted smartphone. In this configuration a tertiary WiFi
interface such as a USB ALFA radio is unnecessary - thus lowering
overall power consumption and increasing run time for battery powered
systems." So adding the extra wlan2 is not necessary. I'm still using wlan2 for client access.
So you bought a new WiFi Pineapple MarkV (MK5), now what?
Assuming you have powered on the MK5 and it has flashed successfully. If not this guide was helpful
http://wiki.wifipineapple.com/#!reset.md
Start with connecting to the MK5. I preferred Kali linux. This was helpful
http://wiki.wifipineapple.com/#!ics.md. I would also make sure you update to the most recent firmware
http://wiki.wifipineapple.com/#!firmware.md.
I started with the many
Hak5 Youtube videos which will get you to a beginning. This helped me understand what to buy also:
1.
MK5
2.
ALFA USB WiFi AWUS036NEH
Why the additional USB WiFi, well that's needed to provide Internet while using PineAP wirelessly.
Getting connected to the MK5.
Attach an Ethernet cable from your computer to the MK5.
The MK5 will provide a DHCP IP to your system.
Open a web browser and go to address: 172.16.42.1:1471
You should be prompted with a welcome screen. Select Continue.
You also might be prompted to ensure you are the physical owner of the MK5. Look at your lights and match.
Select a good password. This will be the password for the root account.
Setup the WiFi connection to your system to manage it via WiFi.
Wait for the reboot
Continue
Login
Initial MK5 front end view
Getting connected to the Internet. Your Network window with an added USB WiFi will boot to the following.
Turn on wlan2.
Select the Network title. This opens the submenu.
Under the client mode --> Join a Network select scan.
Find your network that has Internet access and join. Could be a hot spot from your mobile phone.
Close the window and go back to Network tile and select scan. This will indicate you are connected to the Internet if you can see an IP. This is your outside facing IP for your network. If it fails go back into the Network tab and make sure you entered the correct WiFi password for your network.
Why do we need Internet access? Well if your planning on using PineAP and hosting some stolen access points (AP), it helps to have Internet to keep up the charade.
Now verify you have the most up to date firmware.
If not make sure you update. Check for upgrade.
Flashing the unit again will take you back to the top and getting connected again.
I then decided not to be hack myself and followed this to prevent my own MK5 http clear text passwords from getting stolen.
http://wiki.wifipineapple.com/#!add_ssl.md
I found it also under Sebkinne's GitHub for WiFi Pineapple here
https://github.com/hak5/wifipineapple-wiki/commit/398e44f957e53d41ff132cd29e9394e5a03082be
Log into your MK5 via ssh.
Both necessary directories were already inside /etc/ssl/private and /etc/ssl/certs.
cd /etc/ssl
ls
cp openssl.cnf openssl.cnf.orig
ls
rm openssl.cnf
vi openssl.cnf
i
Paste the following:
dir = .
[ ca ]
default_ca = CA_default
[ CA_default ]
serial = $dir/serial
database = $dir/certindex.txt
new_certs_dir = $dir/certs
certificate = $dir/cacert.pem
private_key = $dir/private/cakey.pem
default_days = 365
default_md = md5
preserve = no
email_in_dn = no
nameopt = default_ca
certopt = default_ca
policy = policy_match
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
default_bits = 2048 # Size of keys
default_keyfile = key.pem # name of generated keys
default_md = md5 # message digest algorithm
string_mask = nombstr # permitted characters
distinguished_name = req_distinguished_name
req_extensions = v3_req
[ req_distinguished_name ]
# Variable name Prompt string
#------------------------- ----------------------------------
0.organizationName = Organization Name (company)
organizationalUnitName = Organizational Unit Name (department, division)
emailAddress = Email Address
emailAddress_max = 40
localityName = Locality Name (city, district)
stateOrProvinceName = State or Province Name (full name)
countryName = Country Name (2 letter code)
countryName_min = 2
countryName_max = 2
commonName = Common Name (hostname, IP, or your name)
commonName_max = 64
# Default values for the above, for consistency and less typing.
# Variable name Value
#------------------------ -----------------------------
0.organizationName_default = Hak5
localityName_default =
stateOrProvinceName_default =
countryName_default = UK
commonName = pineapple
[ v3_ca ]
basicConstraints = CA:TRUE
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer:always
[ v3_req ]
basicConstraints = CA:FALSE
subjectKeyIdentifier = hash
esc
:wq!
Now its time to create the certs. Enter your made up password throughout. Accept the defaults on others.
cd /etc/ssl/certs
openssl genrsa -aes128 -out server.key 2048
openssl genrsa -aes128 -out ca.key 2048
openssl rsa -in server.key -out server.key
openssl req -new -x509 -days 3650 -key ca.key -out ca.pem
openssl req -new -key server.key -out server.csr
below is all one line
openssl x509 -req -days 3650 -in server.csr -CA ca.pem -CAkey ca.key -set_serial 01 -out server.pem
cd /etc/nginx
cp nginx.conf nginx.conf.orig
vi nginx.conf
i
Add the following in
bold:
server {
listen 1471 ssl;
server_name pineapple;
ssl_certificate /etc/ssl/certs/server.pem;
ssl_certificate_key /etc/ssl/certs/server.key;
ssl_protocols SSLv3 TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
Before
After
esc
:wq!
/etc/init.d/nginx restart
If you try to go to the MK5 http site you will not connect.
Now go to https://<MK5 ip>:1471
Accept the self signed connection.
You're in. The encryption should protect you from clear text password reveal.
Before encryption:
After encryption:
Alright that was tedious...
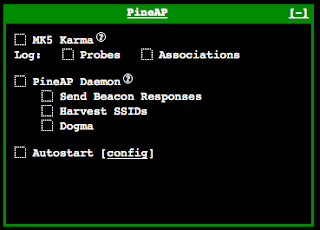
I'll cover PineAP first (v2.3.0). PineAP is a suite of tools.
Karma Attacks Radioed Machines Automatically. KARMA's job is to trick WiFi-enabled devices (i.e. computers,
smartphones, etc.) into connecting to the Pineapple. Here's how it
works: Most devices are continuously searching for networks that they've
previously connected to so they can automatically reestablish a
connection. To do this, the devices send out probe requests. KARMA
listens for those probe requests. When KARMA sees a probe request, it
clones the network that the device is searching for and responds to the
device. In other words, KARMA tricks the device into believing that the
Pineapple is the network that it's looking for. This causes the device
to connect to the Pineapple.
Beacon response is basically the new probe response. It's needed to
exploit devices that are no longer susceptible to the traditional KARMA
probe request/ response method.
Beacon Response will follow up any probe request with a number of beacons.
Harvester is used to harvest information from probe requests. Probe
requests contain information about the access point that the device is
searching for. Harvester collects all SSIDs which can then be used for Dogma.
Dogma gives you the ability to respond to a single probe request or
respond to all probe requests. Before, KARMA would automatically respond
to all probe requests. Dogma helps you to be more target-oriented. Dogma is responsible for sending out the beacons in your SSID list (targeted or to broadcast).
Getting PineAP working.
What are the wlan0, wlan1 and, if purchased, wlan2 doing? Wlan0 pulls in the clients. This is the radio that clients connect to. Wlan1 is put into monitor mode, does beacon responses, beacons, deauth and the likes. Wlan2 or Ethernet can also be used for Internet access while in PineAP mode. I have also been able to use wlan1 to also provide internet.
Under Network lets make sure Wlan0 is on. Wlan1 should be off. If you have Wlan2 turn it on.
On the PineAP tile. Nothing is activated.
Before we turn stuff on lets look at another page. In the upper left hand side of your tiles you will see Infusions and Recon Mode.
Switch to Recon Mode. Recon Mode has many uses but first use is to determine your WiFi and MACs. While using PineAP you do not want to fake your own WiFi.
***I've found that firmware 2.3.0 Karma does not Black list SSIDs well. There is an identified issue where Harvester will harvest your own SSIDs and they will be faked. Recommend the below until v2.4.0 is released.
~~~~~~~~~~~~~~~
Update 20150607; If you want to include a bash script to consistently remove the SSIDs you have every minute you do this:
Under Configuration
Add
"* * * * * /sd/remove_these_ssid.sh" (without quotes)
update crontab
ssh root@172.16.42.1
cd /sd
vi remove_these_ssid.sh
i
add
#!/bin/bash
sed -i '/<SSID>/d' /etc/pineapple/ssid_file
sed -i '/<SSID>/d' /etc/pineapple/ssid_file
sed -i '/<SSID>/d' /etc/pineapple/ssid_file
sed -i '/<SSID>/d' /etc/pineapple/ssid_file
exit 0
esc
:wq!
make sure you change <SSID> to your correct SSID that you do not want to be faked.
make it executable
chmod +x remove_these_ssid.sh
~~~~~~~~~~~~~~~
If you select your WiFi you will be prompted with some choices.
I would recommend Add SSID to Karma filter. If you switch back to Infusions --> PineAP --> Karma --> View List. You should see your SSIDs. Ensure that it in "Currently in Black mode". This is a source of confusion that I have been reading within the forums. Black mode you normally associate with bad and White mode good. In PineAP Black list means OFF and White list means ON. Quote from Sebkinne "You want to
blacklist YOUR laptops /
phones MAC. This means that Karma will NOT act on your MAC. If you were
to whitelist, then it will only work on clients INSIDE the whitelist."
So long as your WiFi SSIDs are in the list under Black mode they will not be faked. This can be good especially if you wanted to target only specific SSIDs. You would change that to Black mode and add the SSIDs. You could also add your MACs above.
Back to the main tiles.
Turn on MK5 Karma. Probes and Associations is optional.
Go into the PineAP tile --> PineAP. Notice the SSID Management. This area will become largely populated within time. It also has direct bearing on location. Meaning if you are in a crowded traffic area with numerous cell phones this list can grow fast. While at a house or apartment and stationary maybe not as fast. What is happening is cell phones, pcs, tablets, thermostats, etc are always trying to connect to WiFi. They will broadcast asking for a connection. PineAP is here to help. It reads those broadcasts and immediately spones an AP for it under the SSID it wants. Those APs are open for the device to connect to.
My OSX is already seeing spawned APs from PineAP. We can see some of the similar APs. Also notice that both my APs WOPR_nomap and 3MTA3_nomap are not being spawned to open APs. This is because of the Black list in Karma and my added cron job. If you attempt to connect to one of these faked APs it will work and you should have internet access.
Now switch over to the clients tab.
Its possible you will start to see some devices connect to your system. You can also attempt to force client to disassociate with their true AP and connect to your. This normally is the case if your fake AP is stronger then the real AP.
Within Recon Mode switch to AP and Clients and scan.
If you hover over the MAC and select the deauth command appears.
If your lucky the MAC will associate under your fake AP.
What then? Tune in next time when I figure that out.